Network diagram flow chart networking data packet gliffy application traffic monitor online business swift example enterprise choose board topology sniffing Nist framework risk overview cybersecurity grc flow implementing using Data flow diagram templates to map data flows nist data flow diagram
NIST Cybersecurity Framework Process View | Beşinci Güç- Siber Güvenlik
Nist framework cybersecurity version gov Nist cybersecurity framework guide Qu'est-ce que le cadre de cybersécurité du nist
Dfd diagrama de flujo pics maesta
Nist sp 800-171 and cmmc level 2 assessment scoping process diagramNetwork diagram examples internet lucidchart create template application structure templates chart database Your guide to fedramp diagramsNetwork diagram examples and templates.
Nist cybersecurity assurance pngkeyNist data flow system ii Conceptdraw samplesGliffy flow chart & diagram online application.

Chart flow nist incident eradication cyber security recovery traduções leituras links
Nist data flow system presentationCyber security leituras, traduções e links: nist flow chart to incident Defense cybersecurity assurance programDiagram pci flow network dss data template diagrams good report business regarding gap creating analysis ideas gelorailmu pray article visit.
Flow dfd flows creately business atmThe road to the horizon: tips & tricks: the network diagram of a blog Flowchart dfd diagrams conceptdraw workflow draw yourdonNist organization chart.

Nist risk management framework template
Nist sp 800 30 flow chartNetwork diagram lucidchart security examples templates topology template wan lan area local chart networking firewall management wide gif storage networks Creating nist-compliant cui data flowsIntroduction to the nist cybersecurity framework for a landscape of.
Nist stream creating iot followsCreating good pci-dss network and data flow diagrams regarding pci dss Data nist flow ii system draft chapter version user guide hosts host transported copies memory shared multiple within across networkLet's demystify the latest nist iot security releases.
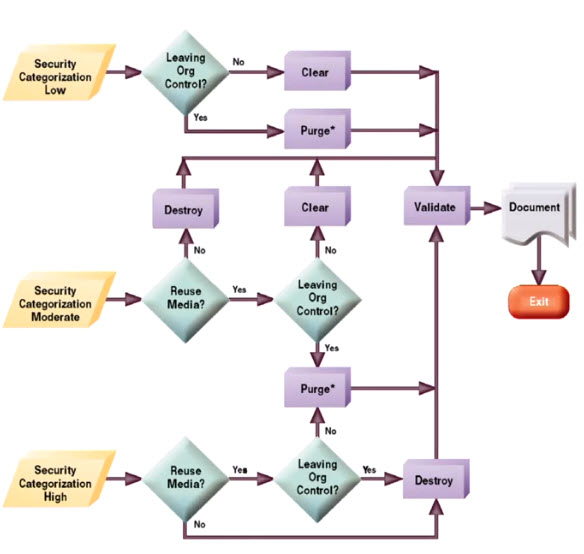
Strengthen security of your data center with the nist cybersecurity
Flow chart of the nist algorithm.A beginner's guide to data flow diagrams Nist cybersecurity framework vs iso vs nist vsDiagram network tips tricks dataflow horizon road.
Nist releases version 1.1 of its popular cybersecurity frameworkCreating a data stream from nist manufacturing lab data – part 1 Risk compliance governance cloud program grc management security template aws framework scaling nist relationship project model plan control cyber organizationNist security iot requirements guidance draft rounding federal demystify releases latest agencies cybersecurity.

Framework nist cybersecurity cyber landscape introduction
The 4 steps for a risk assessment based on nistNist also Network diagram examples and templatesHow to keep your network diagram project right-sized.
(pdf) the nist data flow system ii: a standardized interface forNetwork diagram example project l3 software documentation osp Nist chart organizationUnderstanding and implementing the nist framework.

Understanding the nist cybersecurity framework
Nist cybersecurity framework process viewNist flows example compliant creating regulatory documented dfd Ouline of the use and functions of dfd data flow diagrams writework.
.






